Having multiple AWS accounts is like having a buffet of security and cost management options. You get to enforce controls, enhance your security posture, and streamline audits. It’s like building your own little fort in the cloud, protecting your digital treasures.
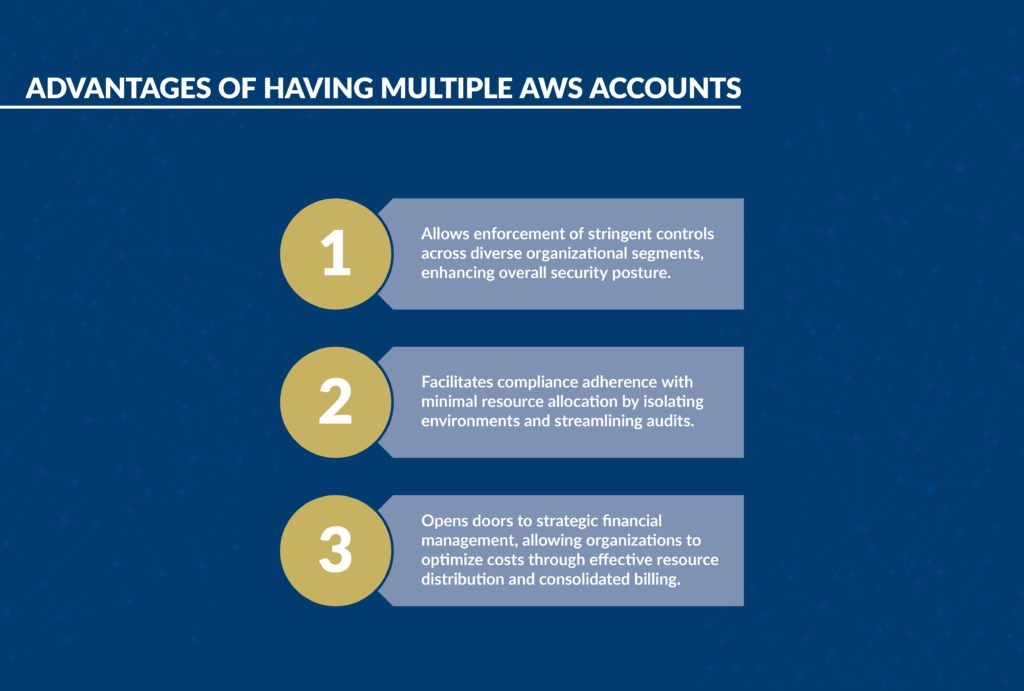
This approach also introduces complexity in oversight and operations. So let’s break down five proven strategies for effectively managing multiple AWS accounts in AWS Organizations.
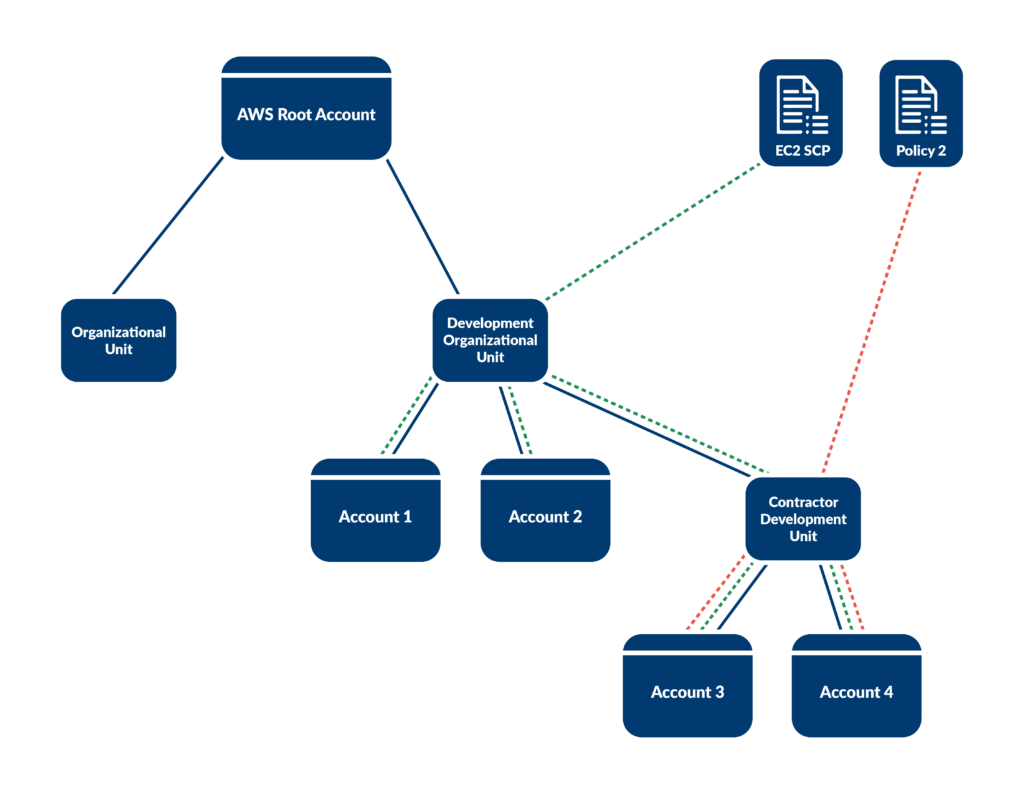
1. Use Service Control Policies (SCPs) at the OU level
Organizational Units (OUs) allow you to group multiple AWS accounts together, making applying policies to multiple accounts easier. They are essential for structuring your AWS environment in a hierarchical, manageable manner.
Using SCPs will enable you to centralize permissions management. They apply limits across the entire organizational unit or account level, meaning that every IAM user and role in each account will inherit the limitations from the SCP.
Because accounts within the OU inherit these policies, you only need to change an SCP once to update all accounts and increase or decrease permissions.
Practical Application: Using SCPs at the OU level
A company restricts the usage of EC2 instances of certain types in the “Development” OU to control costs. They create an SCP that denies the usage of EC2 instances of type m5.2xlarge and apply it to that OU. Now, regardless of permissions, no developers can apply an m5.2xlarge EC2 instance, which can help reduce costs without requiring manual intervention.
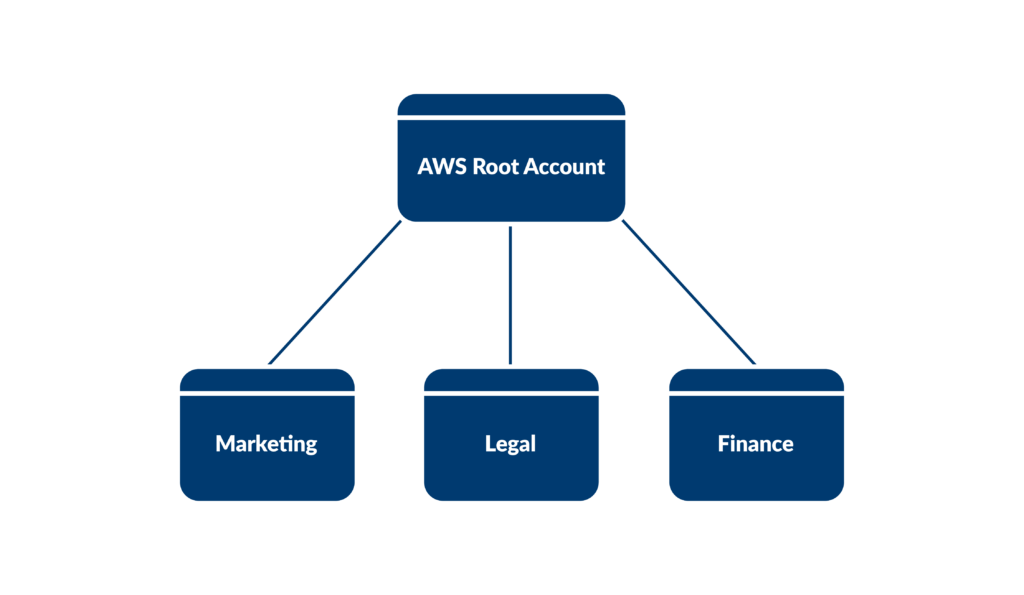
2. Split accounts based on function
Splitting accounts is core to AWS’s security pillar. Following the principle of least privilege allows you to keep departmental teams isolated to only the resources they need access to. This can be an added layer of security to isolate access beyond just provisioning SCPs and managing access through IAM roles.
Practical Application: Splitting accounts based on function
An organization has HR, Finance, and Development each use different accounts specific to their department, allowing for clearer separation of concerns, easier tracking of resource usage, and more granular control over access and permissions. Now the risk of someone from HR accidentally getting access into the Finance department’s general ledger is significantly reduced.
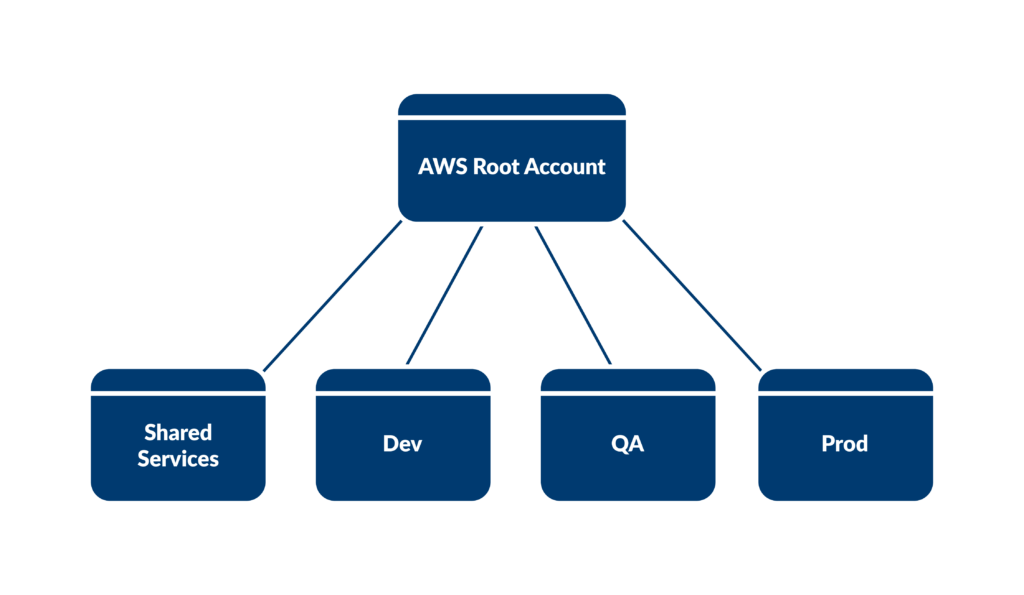
3. Contain development environments into separate accounts
Different environments like production, staging, and development serve distinct purposes in the software development lifecycle. Segregating these environments into separate accounts ensures isolation, reducing the risk of unintended interactions and conflicts.
Use AWS CodeCommit to create deployment pipelines that can push your development through accounts into different environments. This ensures that your code is tested and stable before it moves from development to production.
This approach also has the benefit of cost optimization, as lower environments do not need to have as many resources as higher environments. This allows you to test in dev at a lower cost without interfering with production data or performance.
Practical Application: Splitting development environments into separate accounts
Reducing the size of an Amazon Redshift cluster in a staging environment can help in estimating both cost and performance implications before implementing changes in the production environment.
4. Use consolidated billing to simplify cost and payment management
AWS Organizations provide consolidated billing that has several benefits:
- Unified view of costs
- Consolidated billing allows users to view incurred across all accounts in the organization.
- This simplifies the payment process and enables effective cost monitoring and management.
- Cost estimation
- Having an aggregate view of all costs enables users to generate cost estimates more effectively
- This also ensures that resources are utilized efficiently without unnecessary expenditures.
- Volume discounts
- Companies that consume larger amounts of resources at an aggregate can receive discounts compared to if they had each account billing separately.
- Read more about volume discounts here.
- Single payment source
- Organizations using consolidated billing can have a single payment method for all accounts.
- This reduces administrative overhead and simplifies the payment process, allowing organizations to focus more on strategic activities.
- Note: AWS does not natively support the ability to have each account in an organization use a separate payment method. If someone wanted to pay separately, they would need to move those accounts into a separate Organizational Unit, which would mean that the user would no longer receive benefits such as aggregated cost estimation, volume discounts & a unified view of costs.
Practical Application: Using AWS Consolidated Billing
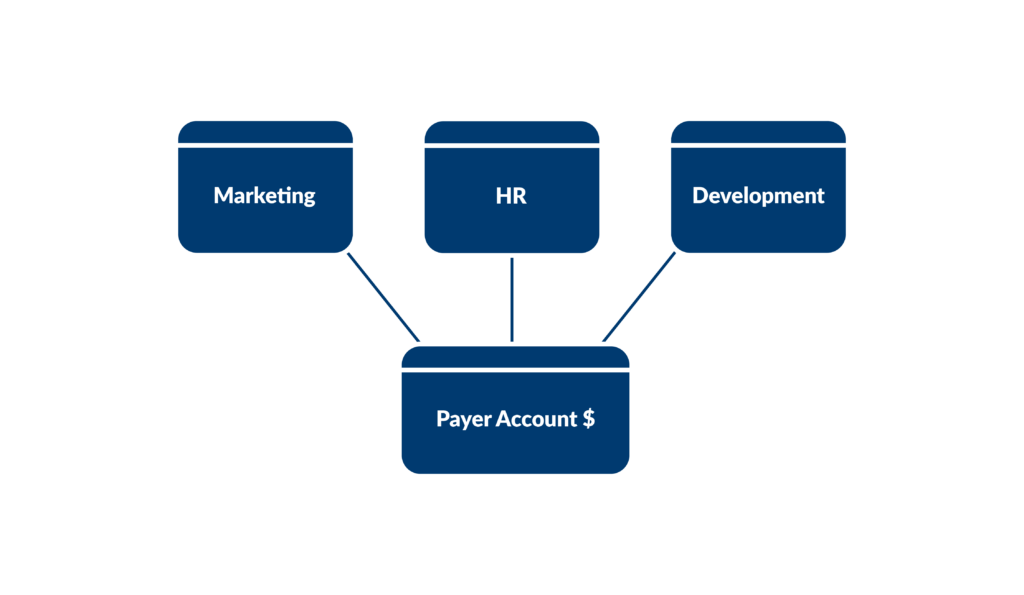
A company utilizes AWS Organizations to structure resources across separate accounts for each department (e.g., Marketing, HR, Development) and branch (e.g., USA, UK, India). By leveraging consolidated billing, all the AWS usage charges across these accounts are rolled up to a single-payer account, simplifying the payment process and enabling the company to easily track and manage costs. This setup not only provides a unified view of AWS charges but also allows the company to take advantage of pricing benefits, such as volume discounts, by aggregating usage from all accounts, thereby optimizing costs across the entire organization.
5. Automate and streamline account setup with AWS Control Tower
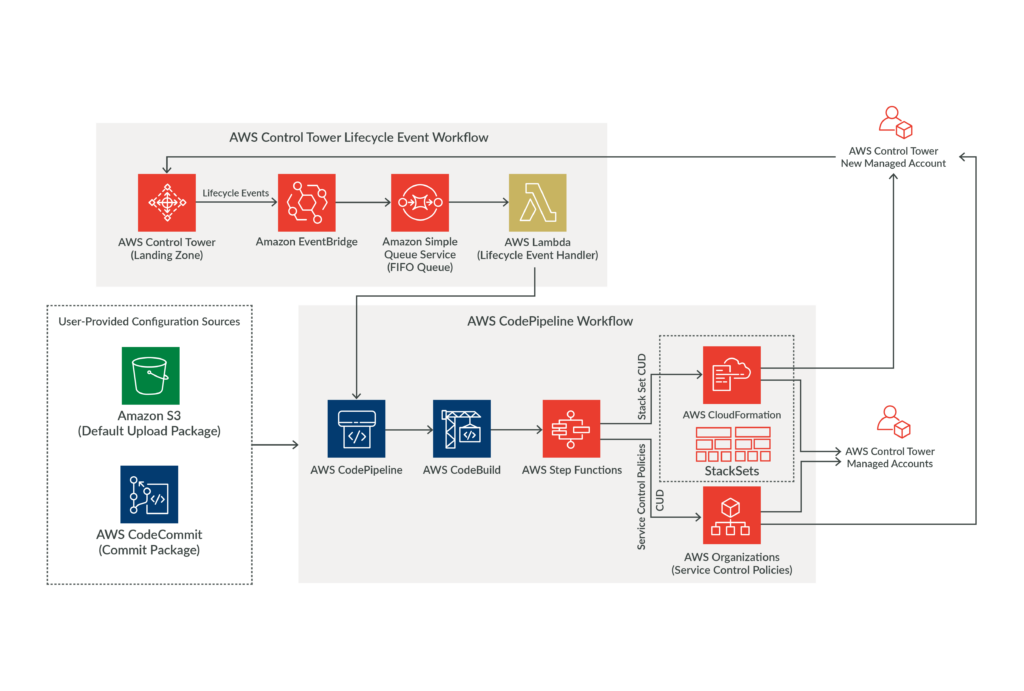
AWS Control Tower offers the easiest way to set up and govern a secure, compliant, multi-account AWS environment. It automates the setup of a well-architected multi-account AWS environment, applying best practices from AWS’s years of experience.
AWS Control Tower enables organizations to quickly set up their AWS environment with predefined security and compliance controls, allowing them to start building in AWS in a secure and compliant manner.
How to set up and use Control Tower
- Access AWS Control Tower
- Log in to the AWS Management Console.
- Navigate to AWS Control Tower.
- Set up Landing Zone
- In AWS Control Tower, choose “Set up landing zone.”
- Provide the necessary information such as email addresses for AWS SSO users, and choose the region
- Review and confirm the setup information.
- AWS Control Tower will create a landing zone which includes setting up AWS Organizations, AWS SSO, and pre-configured governance rules (Guardrails).
- Create Organizational Units (OUs)
- Once the landing zone is set up, create Organizational Units (OUs) to group AWS accounts with similar purposes.
- Assign governance guardrails to OUs to enforce policies.
- Enroll or Create AWS Accounts
- Enroll existing AWS accounts or create new AWS accounts within the OUs.
- AWS Control Tower will apply the guardrails to the accounts based on their assigned OUs.
- Monitor and Manage
- Regularly monitor the AWS Control Tower dashboard for any non-compliant resources or accounts.
- Manage user access through AWS SSO.
- Continuously review and update guardrails as per the compliance and security requirements.
Remember, AWS Control Tower is designed to set up and govern a secure and compliant multi-account environment, and it’s crucial to regularly review and update the configurations to align with the evolving business requirements.
Practical Application: Using AWS Control Tower
A company leverages AWS Control Tower to manage and govern its multi-account AWS environment securely. The company sets up a landing zone using Control Tower which automatically creates a well-architected multi-account AWS environment, complete with predefined security and compliance guardrails.
This streamlined service allows the company to easily manage various workloads, such as application development, data analytics, and customer-facing services, each in isolated AWS accounts, while ensuring adherence to security and compliance requirements.
The company can also provision new AWS accounts seamlessly, adhering to the company’s organizational policies and best practices, thereby ensuring a secure and compliant environment as the startup scales and evolves. This approach significantly reduces the operational overhead and accelerates their cloud adoption journey by providing a governance framework that is easy to set up and manage.
Final thoughts
These are five best practices, but managing multiple accounts can become complicated. For further insights and in-depth knowledge of AWS Organizations and its best practices, selecting an AWS Partner like 27Global is a secure option to work with experts in multi-account intricacies. Contact one of our solution architects here.

Nate C. is a software consultant with a background in data science and organizational psychology. He has a proven track record in product and software development across various industries. Outside of work, Nate enjoys endurance sports, learning new languages, and skiing, balancing his professional achievements with active personal pursuits.






